
For industry-leading, context-aware data loss prevention (DLP), Endpoint Protector from CoSoSys is an advanced tool that works across Windows, macOS and Linux.
Users reduce the chance of both financial damage and regulatory compliance failures with Endpoint Protector benefits including:
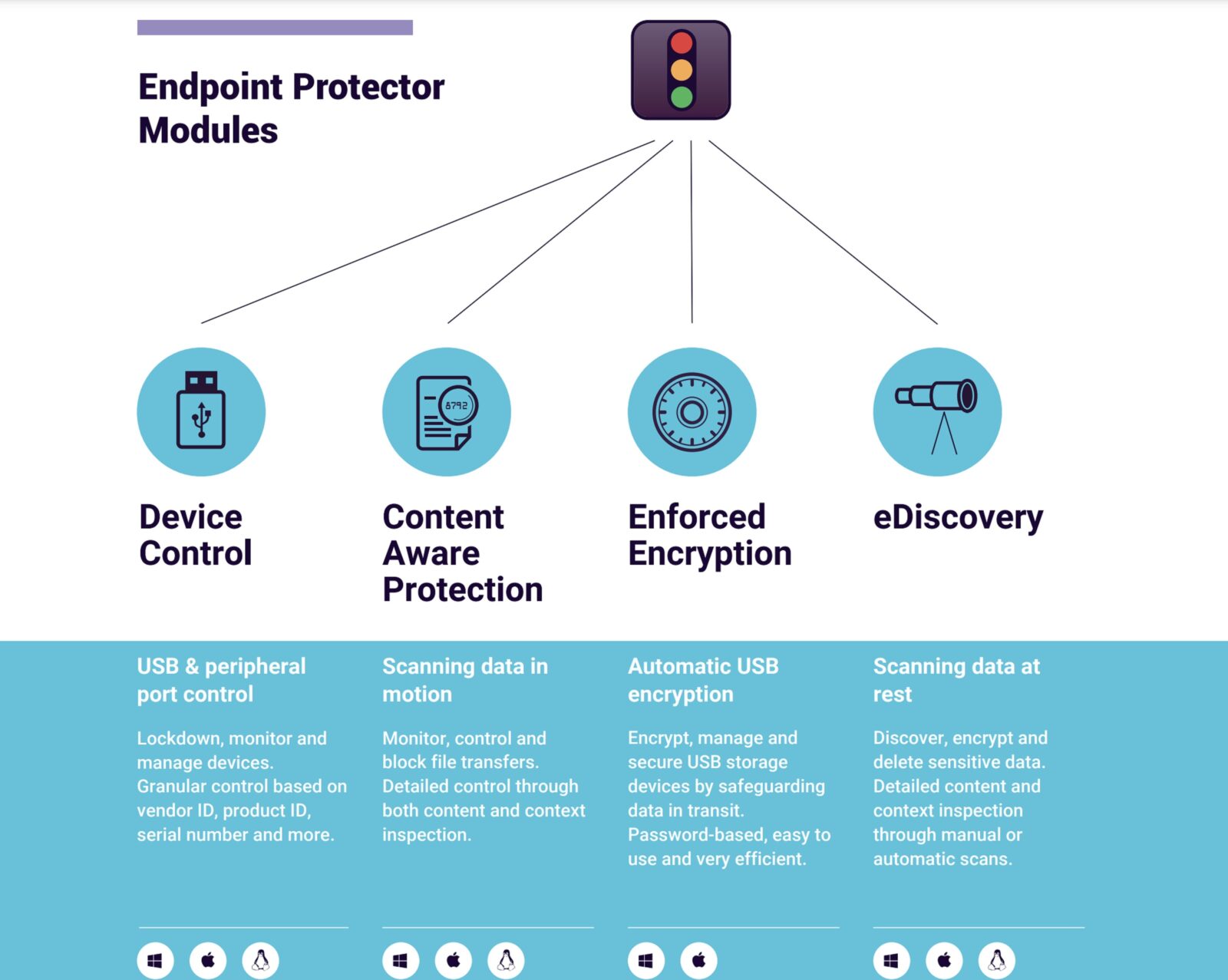
- Monitoring, controlling and blocking of unauthorised file transfers.
- Enforcement of encryption policies right to the endpoint.
- Identifying sensitive data wherever it sits in the organisation via discovery functionality.
APPLY PROVEN DLP TECHNIQUES
In tough economic times especially, today’s businesses cannot afford to take chances on leaks and losses of data and information, which can result in enormous financial losses, from regulator fines to costs of breach remediation and consequent legal fees. In some cases, fines alone can amount to millions of pounds, seriously limiting organisational agility.
That’s before you even consider the potential damage done by data and information exposure to individuals, including customers.
Proven techniques that prevent data leaks exist, whether the breach stems from deliberate targeting or simply human error. Generally, best practice involves combining techniques, tools and strategies for the most assured approach, whether the vector of attack is a single inbox or a corporation-wide database.
Breaches can involve disclosure or theft an array of data types.
- Personally identifiable information (PII).
- Healthcare data.
- Financial records.
- Competitive business information.
- Intellectual property (IP).
EIGHT STEPS TO DLP SUCCESS
- Data discovery and classification tools for scanning all storage, databases and servers. Inventory all data and identify sensitive data wherever it is located – a major issue in large organisations especially. Watch out for unassigned ownership of data – assign owners for better management and monitoring – and unsecured cloud storage that’s publicly available as well. For instance, N-gram-based text categorisation accurately discovers intellectual property (IP) including source code concealed within myriad file formats
- Context-aware DLP tools. The right choice here can monitor data movement in relation to how it is used, adjusting controls based on informational sensitivity and the role of the user in question. With these tools, you can easily block unauthorised data transfers and defend the organisation against data exfiltration – a growing trend in 2024.
- Proactive monitoring and real-time response functionality. When you can observe network, systems and data at all times, it’s easier to detect anomalies and threats – before they result in leakage or systems failure. This means adopting and deploying tools that offer advanced analytics, incorporating AI/ML which can assist with identifying variations in network behaviour. Real-time threat intelligence and detailed logs can be integrated with SIEM tooling, helping ensure the organisation stands ready to mitigate and counter threats – especially if automated tools and scripts are incorporated to isolate systems, revoke access and apply patches as required.
- Secure web gateways. These are useful for blocking access to malicious websites and content, helping fend off phishing and malware. Remember that data can also be stolen if stored in web browsers, email clients, instant messaging apps and so on.
- Deliver solid security awareness training. With human error and lack of understanding key to many breaches, all tooling needs to be backed up with appropriate training for all staff, regardless of level of involvement or pay grade, including education on best practices in data handling or systems use, company security policies, incident reporting, remote working, and device use.
- Adopt robust authentication and full encryption. Usernames and passwords aren’t sufficient. Multi-factor authentication (MFA), ideally with biometrics or hardware token-based authentication, is critical. Choose adaptive authentication mechanisms that adjust authentication based on location, devices, times, and resources used. Meanwhile, all data should be encrypted, whether in transit or at rest, and where transferring over a network or between devices and systems is needed, adopt secure communication protocols (such as SSL/TLS, SSH, and VPN).
- Manage third-party risk across supply chains. The MOVEit incident in 2023, for example, resulted in supply chain breaches at 2,600 companies. Look across all software used, inventorying and analysing third party products and services.
- Adopt zero-trust principles. Avoid trust by default of any user, app, or service, regardless of location. Always apply micro-segmentation to verify all users, devices, and system interactions before granting access. This minimises the attack surface, including between different systems and devices. Real-time security policies can adapt based on the context of access requests.
Endpoint Protector by CoSoSys, with its device control, e-discovery, context-aware protection, and enforcement of encryption modules, can help any organisation meet these best-practice targets for DLP – check out their free guide to best practice, available here.
NO ONE WANTS TO BE THE NEXT EQUIFAX
Major brands from Equifax to Yahoo! and Capital One have already suffered extreme reputational damage and financial losses as a result of data breaches that could have been tackled with strong DLP solutions. The Equifax breach in 2017, for example, hit some 143 million users after an attacker escalated access via an unpatched customer web portal.
Customer organisations can easily discover, monitor, and protect all sensitive data with Endpoint Protector from CoSoSys – and advanced multi-OS DLP offering for continual protection and insights into network, systems and device data for better management and defences, whether online or offline. In addition, Endpoint Protector by CoSoSys helps organisations achieve compliance with various industry standards including HIPAA, PCI-DSS, NIST, GDPR and SOX.
AWARD-WINNING DLP FROM COSOSYS
In 2023 alone, CoSoSys won the Enterprise Data Loss Prevention category at the Globee Awards for Information Technology as well as the Cutting Edge DLP Global InfoSec Award sponsored by Cyber Defense Magazine.
Endpoint Protector by CoSoSys was also the Gold Winner in the DLP Europe category at the 2023 Cybersecurity Excellence Awards.
Contact
Christian Röttig
Product Manager
📞 +49 89 2314142 69
✉️ christian.roettig@qbssoftware.de
(Photo by John Matychuk on Unsplash)
